Difference between revisions of "UCSB CTF 2004"
(→What To Do Better) |
(→What To Do Better) |
||
| Line 7: | Line 7: | ||
== What To Do Better == | == What To Do Better == | ||
| − | + | === General === | |
* don't put such a strong focus on host and network security again, this game was about application security ... | * don't put such a strong focus on host and network security again, this game was about application security ... | ||
* use some means of internal communication (wiki?) | * use some means of internal communication (wiki?) | ||
| Line 13: | Line 13: | ||
Research would read code, produce new exploit and fix bugs. | Research would read code, produce new exploit and fix bugs. | ||
Abuse would automate and use exploits. | Abuse would automate and use exploits. | ||
| + | |||
| + | === VMWare Game Image Security === | ||
| + | Check for | ||
| + | * ssh pubkeys | ||
| + | * sshd configuration: | ||
| + | ** PubKeyAuthentication | ||
| + | ** PermitRootLogin | ||
| + | * nfs exports | ||
| + | * user passwords | ||
| + | ** PHP Safe Mode? | ||
== Pics! == | == Pics! == | ||
Revision as of 00:55, 6 December 2004
A team of hackers (known as "0ld Eur0pe"), mainly consisting of the Summerschool Aachen 2004, members of the Chaos Computer Club Cologne and some students of the RWTH[1], participated in the UCSB Capture The Flag 2004 game and were quite successful (see the scoreboard[2], second line).
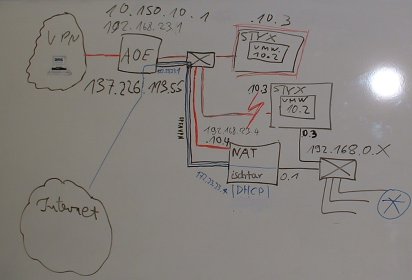
This page serves as a whiteboard to document the setup we used this year and to collect ideas about what we can do better next time.
Setup
What To Do Better
General
- don't put such a strong focus on host and network security again, this game was about application security ...
- use some means of internal communication (wiki?)
- split teams into research/abuse instead of attack/defense (?)
Research would read code, produce new exploit and fix bugs. Abuse would automate and use exploits.
VMWare Game Image Security
Check for
- ssh pubkeys
- sshd configuration:
- PubKeyAuthentication
- PermitRootLogin
- nfs exports
- user passwords
- PHP Safe Mode?