Difference between revisions of "UCSB CTF 2004"
(→VMWare Game Image Security) |
(→What To Do Better) |
||
| Line 23: | Line 23: | ||
* user passwords | * user passwords | ||
* PHP Safe Mode? | * PHP Safe Mode? | ||
| + | |||
| + | === Patches and Exploits === | ||
| + | Please contribute the weaknesses you found including exploits and patches. | ||
| + | Lexi is also collecting all files that were produced during the event (scripts, logs, etc) | ||
| + | * pollit | ||
| + | ** directory traversal, rsutling is reading and writing capability on files whose names contain a dot | ||
| + | * register | ||
| + | ** possible SQL-injection in at least update.pl and review.pl due to unsanitized input | ||
== Pics! == | == Pics! == | ||
Where are the pictures people made during the event? Where can I download the video somebody created? | Where are the pictures people made during the event? Where can I download the video somebody created? | ||
Revision as of 09:51, 6 December 2004
A team of hackers (known as "0ld Eur0pe"), mainly consisting of the Summerschool Aachen 2004, members of the Chaos Computer Club Cologne and some students of the RWTH[1], participated in the UCSB Capture The Flag 2004 game and were quite successful (see the scoreboard[2], second line).
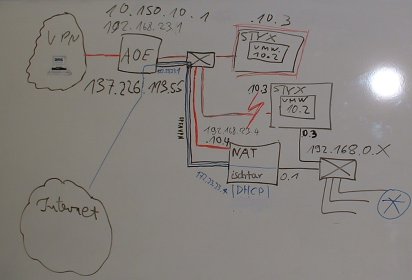
This page serves as a whiteboard to document the setup we used this year and to collect ideas about what we can do better next time.
Contents
Setup
What To Do Better
General
- don't put such a strong focus on host and network security again, this game was about application security
- use some means of internal communication (wiki?)
- split teams into research/abuse instead of attack/defense (Research would read code, produce new exploit and fix bugs, Abuse would automate and use exploits) (?)
- start earlier
- get more hardware boxes which could be used for monitoring and firewalls
VMWare Game Image Security
Check for
- ssh pubkeys
- sshd configuration:
- PubKeyAuthentication
- PermitRootLogin
- nfs exports
- user passwords
- PHP Safe Mode?
Patches and Exploits
Please contribute the weaknesses you found including exploits and patches. Lexi is also collecting all files that were produced during the event (scripts, logs, etc)
- pollit
- directory traversal, rsutling is reading and writing capability on files whose names contain a dot
- register
- possible SQL-injection in at least update.pl and review.pl due to unsanitized input
Pics!
Where are the pictures people made during the event? Where can I download the video somebody created?