|
|
| (20 intermediate revisions by 18 users not shown) |
| Line 1: |
Line 1: |
| − | A team of hackers (known as "0ld Eur0pe"), mainly consisting of the [[Summerschool Aachen 2004]], members of the [[Chaos Computer Club Cologne]] and some students of the RWTH[http://www.rwth-aachen.de], participated in the UCSB Capture The Flag 2004 game[http://www.cs.ucsb.edu/~vigna/CTF/] and were quite successful (see the participants[http://www.cs.ucsb.edu/~vigna/CTF/participants.html] and scoreboard[http://kurosawa.cs.ucsb.edu/cgi-bin/scoreboard.py], second line).
| |
| − |
| |
| − | This page serves as a whiteboard to document the setup we used this year and to collect ideas about what we can do better next time.
| |
| − |
| |
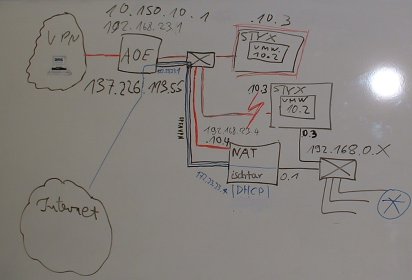
| | == Setup == | | == Setup == |
| | [[Image:NetworkSetup.jpg|Image:NetworkSetup.jpg|Network Setup]] | | [[Image:NetworkSetup.jpg|Image:NetworkSetup.jpg|Network Setup]] |
| Line 8: |
Line 4: |
| | The image is missing our loghost, which we added later with a hub in front of styx. | | The image is missing our loghost, which we added later with a hub in front of styx. |
| | | | |
| − | == What To Do Better ==
| + | [[Category:Events]] |
| − | === General ===
| |
| − | * don't put such a strong focus on host and network security again, this game was about application security
| |
| − | * use some means of internal communication (wiki?)
| |
| − | * split teams into research/abuse instead of attack/defense (Research would read code, produce new exploit and fix bugs, Abuse would automate and use exploits) (?)
| |
| − | * start earlier
| |
| − | * get more hardware boxes which could be used for monitoring and firewalls
| |
| − | * doorkeeper for drunken people
| |
| − | | |
| − | === VMWare Game Image Security ===
| |
| − | Check for
| |
| − | * ssh pubkeys
| |
| − | * sshd configuration:
| |
| − | ** PubKeyAuthentication
| |
| − | ** PermitRootLogin
| |
| − | * nfs exports
| |
| − | * user passwords
| |
| − | * PHP Safe Mode?
| |
| − | | |
| − | === Patches and Exploits ===
| |
| − | Please contribute the weaknesses you found including exploits and patches.
| |
| − | Lexi is also collecting all files that were produced during the event (scripts, logs, etc)
| |
| − | * pollit
| |
| − | ** directory traversal, rsutling is reading and writing capability on files whose names contain a dot
| |
| − | * register
| |
| − | ** possible SQL-injection in at least update.pl and review.pl due to unsanitized input
| |
| − | * feedback
| |
| − | ** directory traversal, ability to write (append) and read access to script files. Appending leads to executing of malicious commands.
| |
| − | | |
| − | == Pics! ==
| |
| − | | |
| − | Where are the pictures people made during the event? Where can I download the video somebody created?
| |
| − | (That was Klaus Ridder)
| |
| − | | |
| − | == Logs ==
| |
| − | | |
| − | fd0 has some irc-logs of #ucsb-ctf on freenode during the game.
| |